Site-to-Site VPN: Connecting AWS with Azure
Why And When Do We Need?
We need a VPN when workloads are distributed across various cloud providers (i.e., Azure and AWS). In our case, the VPN need arises when resources on this platform are private and cannot be accessed outside the cloud by default. So, we need it to allow workloads across these platforms to communicate securely over the public internet.
Terminologies You Need To Know
- VPN
A Virtual Private Network (VPN) establishes a secure network connection between devices via the Internet. It allows for the safe and anonymous transmission of data across public networks. VPNs achieve this by concealing user IP addresses and encrypting data to prevent unauthorized access.
2. VPN tunneling
This refers to the method by which VPN packets reach their designated destination, often a private network.
3. IPSec
IPSec encompasses a collection of communication protocols designed for establishing secure connections over a network.
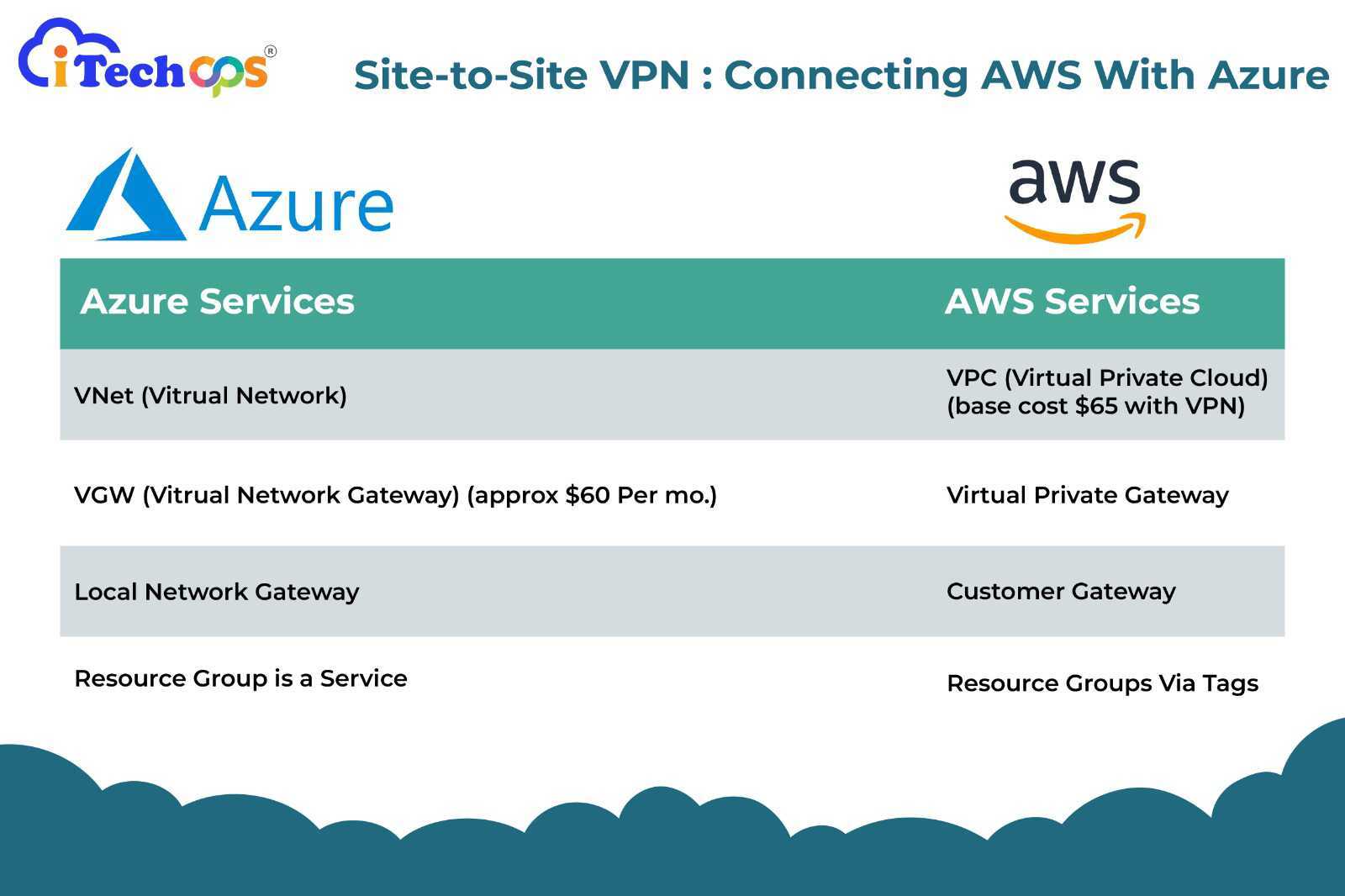
For Azure Services, We Require:
1. Resource Group
2.VNet associated to the resource Group
3. Virtual Gateway attached to VNet for Secure Communication
For AWS Services, We Require:
1. Virtual Private Cloud – By default, there is one created for each region
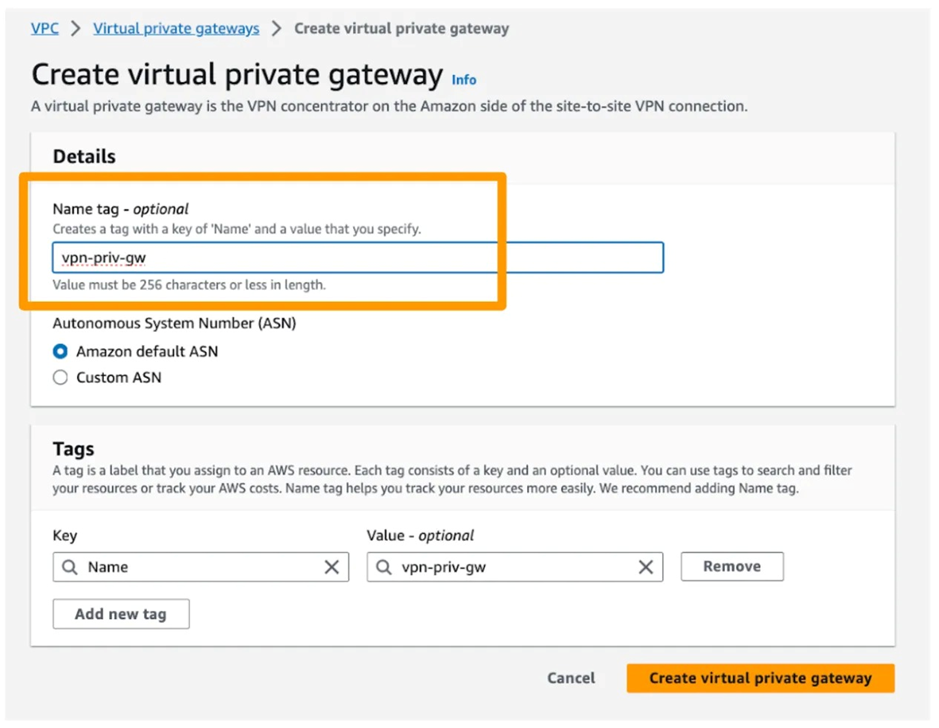
2. Virtual Private Gateway – It handles private connections made through VPN
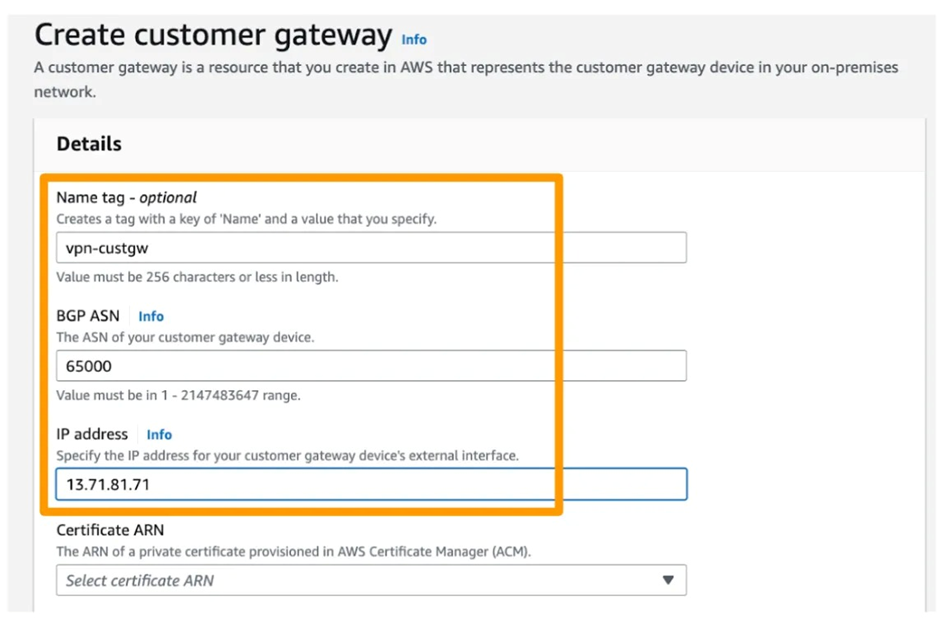
3. Customer Gateway- It accepts connections from Azure VGW.
NOTE: An architectural diagram is provided at the end of the reference section below for in-depth understanding.
Steps To Implement It:
1. Create a Resource Group in Azure (Optional if you have one)
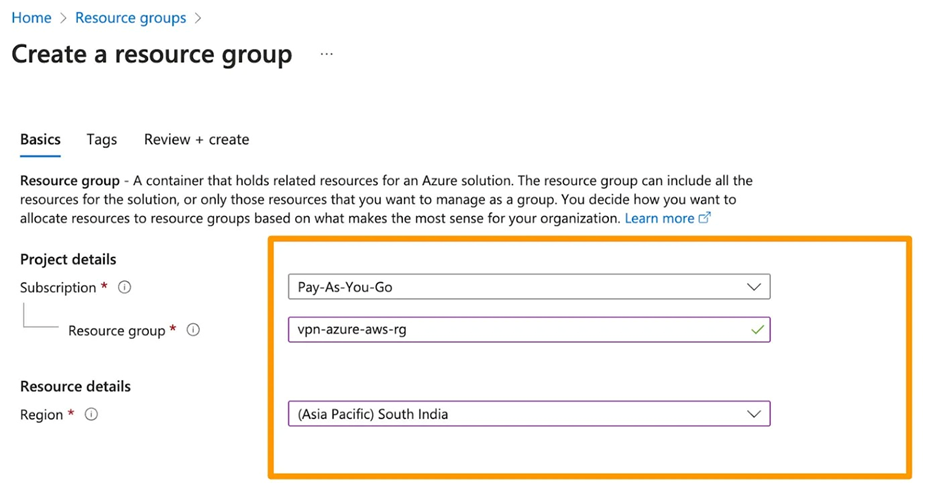
2. Create a VNet and Subnet in the existing one or newly created RG (Resource Group)
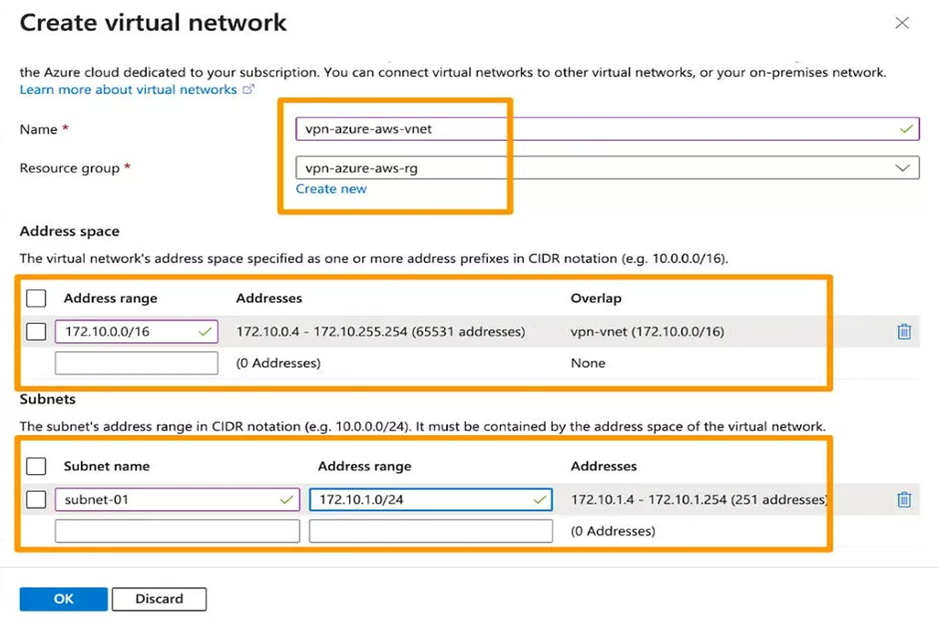
3. Create a Virtual Network Gateway (VGW) and select the above-created VNet for it.
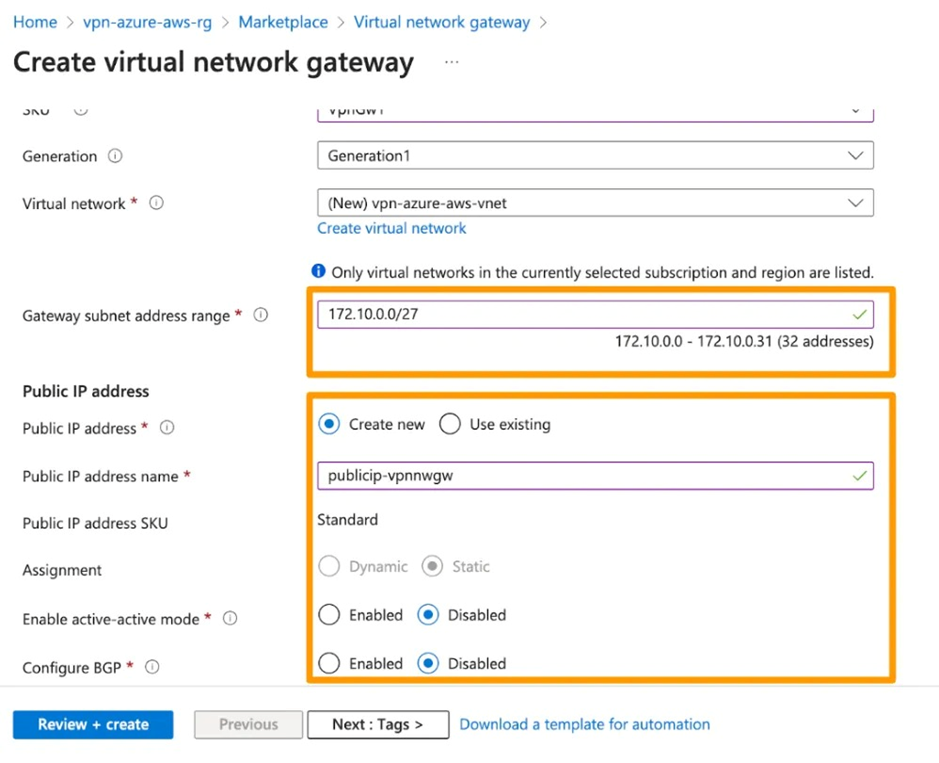
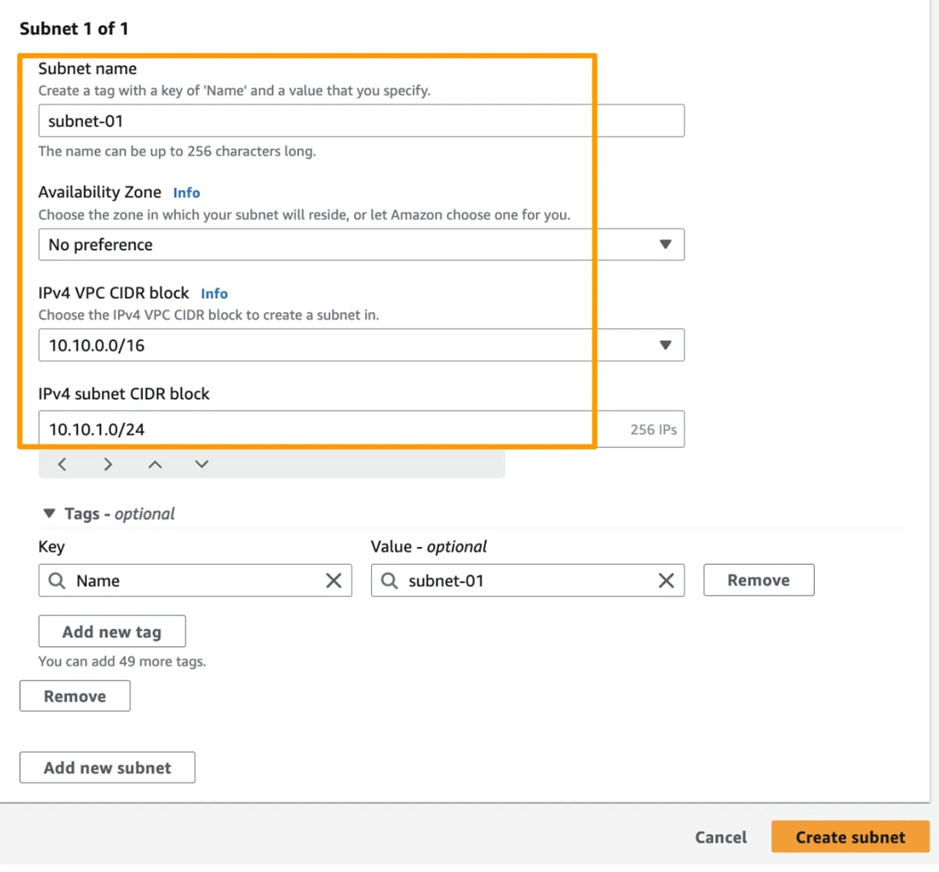
4. Create an AWS Virtual Private Gateway (VPC) and associate a Subnet to it.
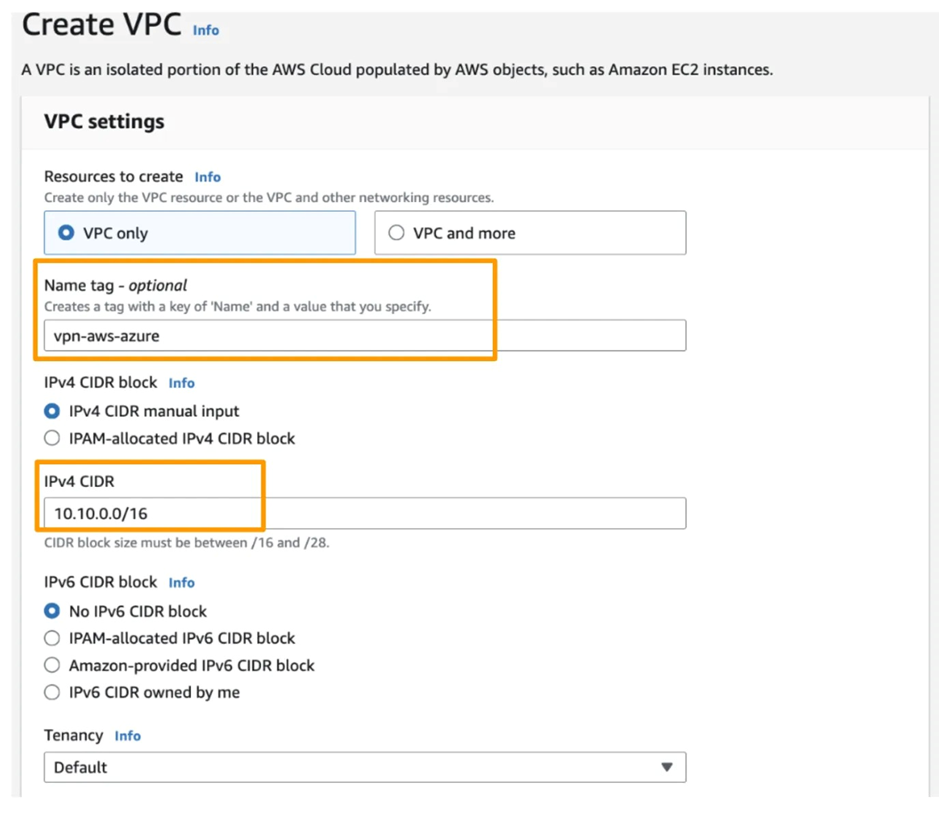
5. Create AWS CGW (Customer Gateway) with the Public IP of Azure VGW.
6. Create a Virtual Private Gateway (VPG) and select/attach to the above create VPC for it in AWS.
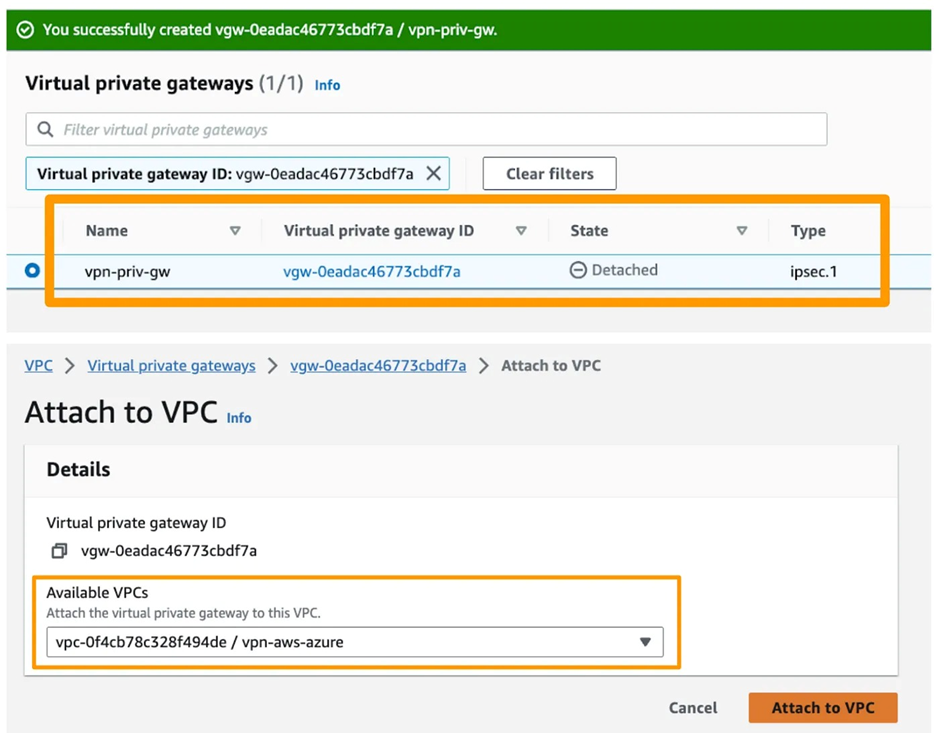
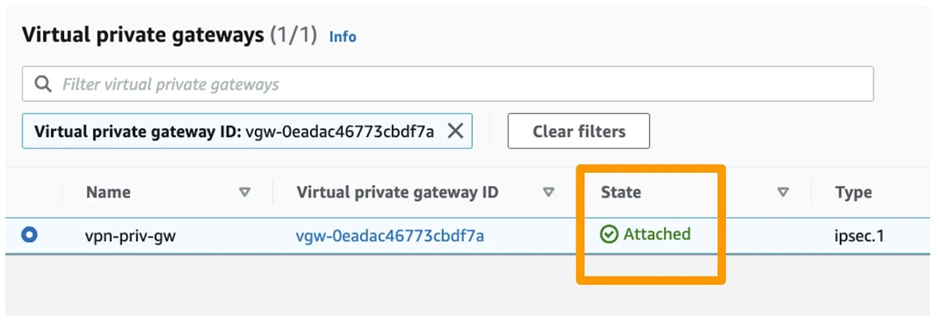
7. Now, in AWS, create a Site-to-Site VPN. Navigate to VPC > VPN Connection > Create a new connection. Select the existing VPN and CGW that we created earlier. For the Routing Option, choose Static and provide the Azure Subnet range.
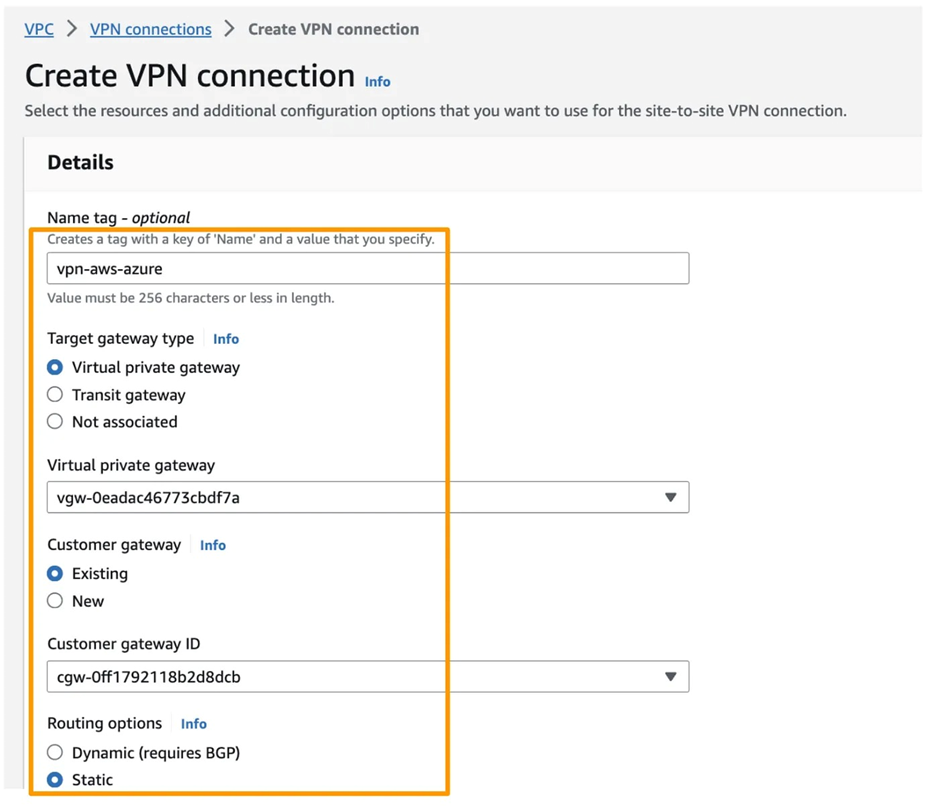
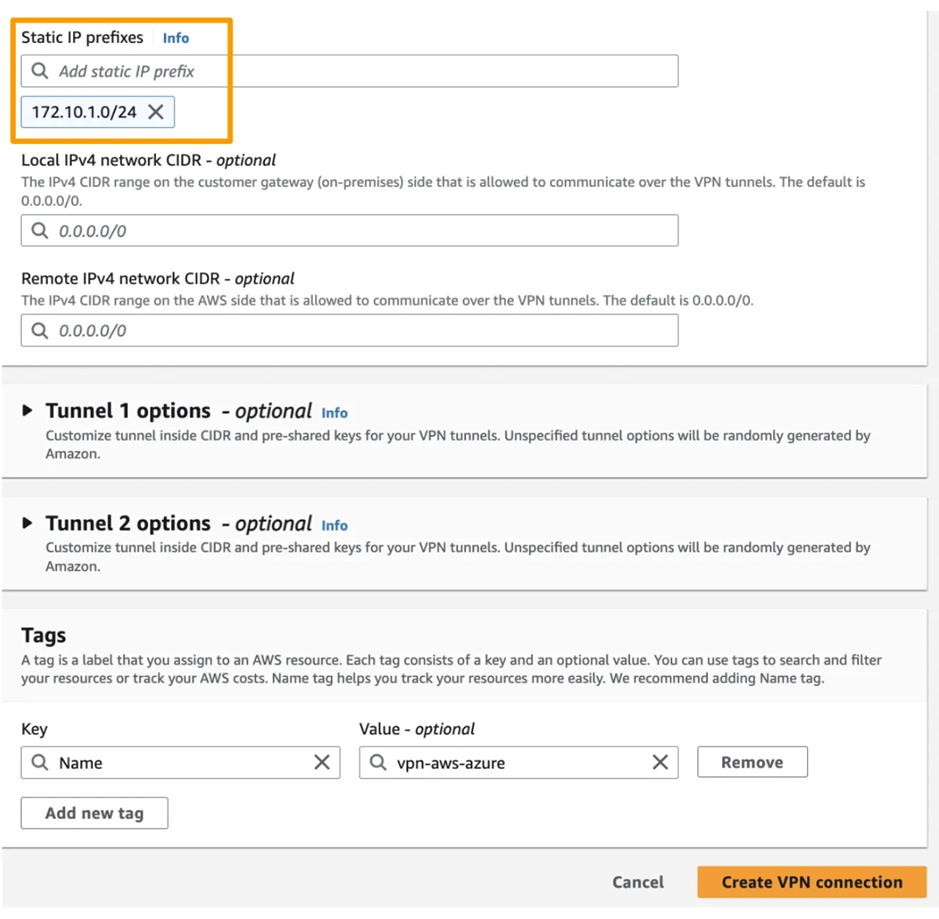
8. After creating this VPN Connection on AWS, download the configuration file, which contains information about tunnel keys and IP addresses.
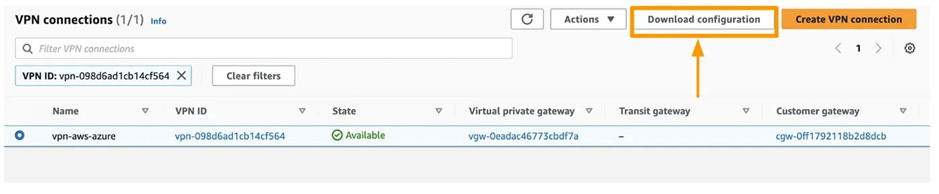
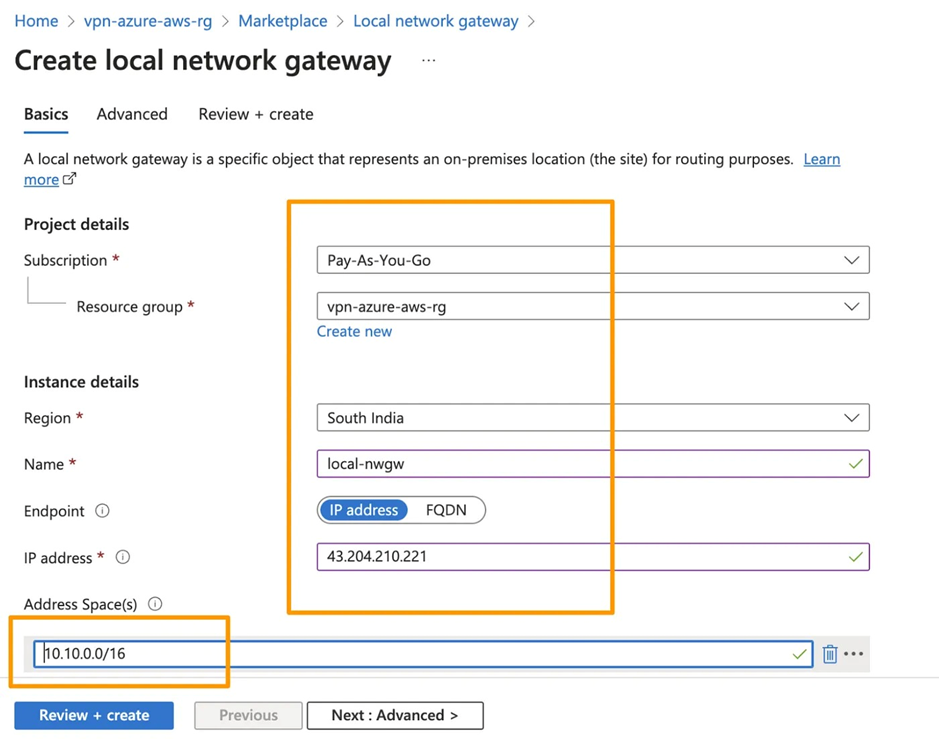
9. Use this configuration on Azure to create a Local Network Gateway (LGW) for each tunnel. In the “IP address” section, please input the IP values specified in the VPN Configuration file. For Tunnel #1, locate these values in the Tunnel Interface Configuration under Outside IP Addresses, specifically under Virtual Private Gateway.
Note: In the “Address Space(s)” field, enter the AWS VPC CIDR Range, which is typically 10.10.0.0/16.
10. Now, create a connection using Azure Virtual Network Gateway. Please select the Virtual Network Gateway and Local Network Gateway that were created in the preceding step. You can obtain the Shared Key (PSK) from the VPN Configuration file, specifically under the corresponding IPSec Tunnel section, labeled as Pre-Shared Key.
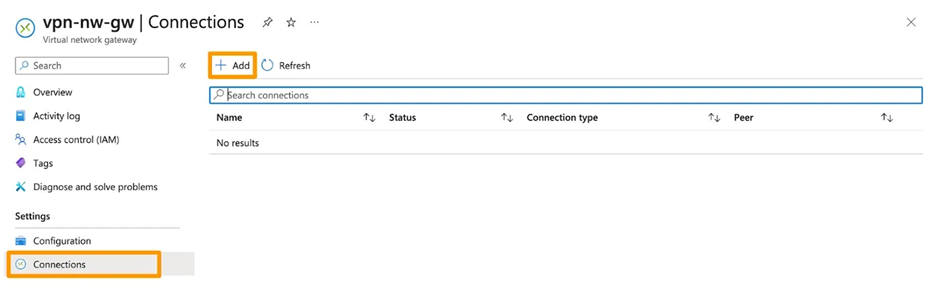
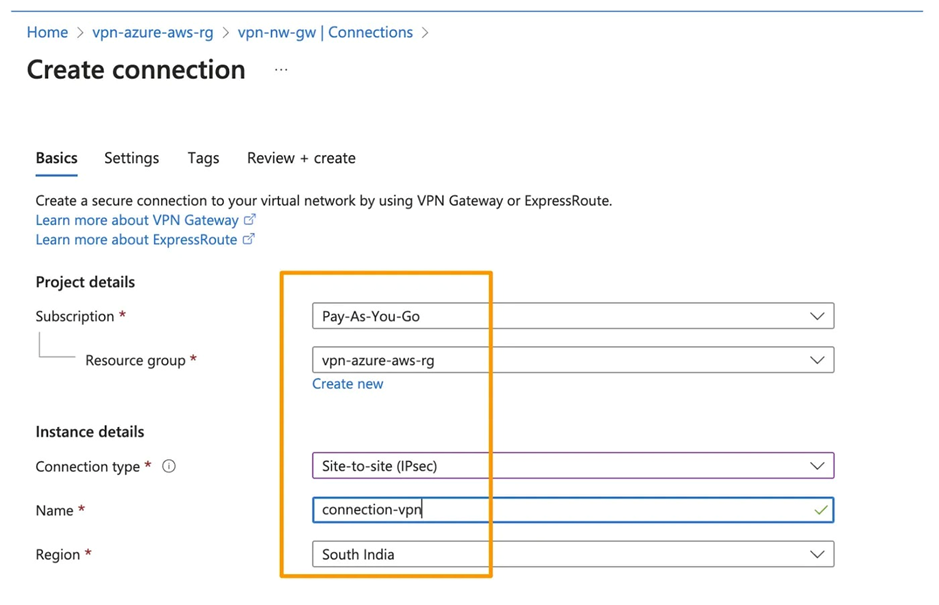
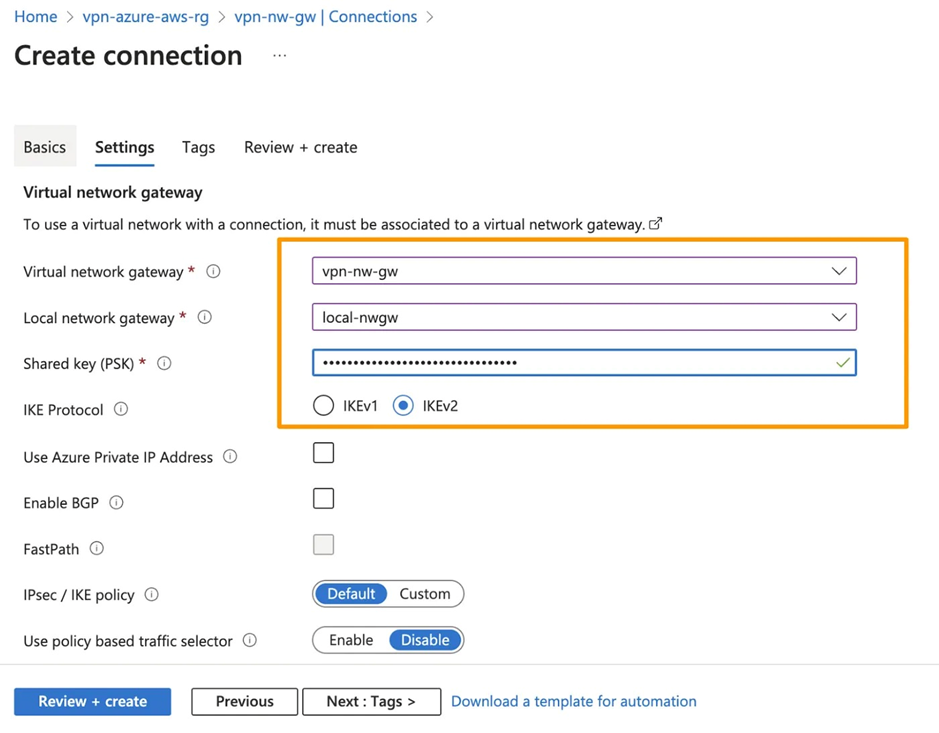
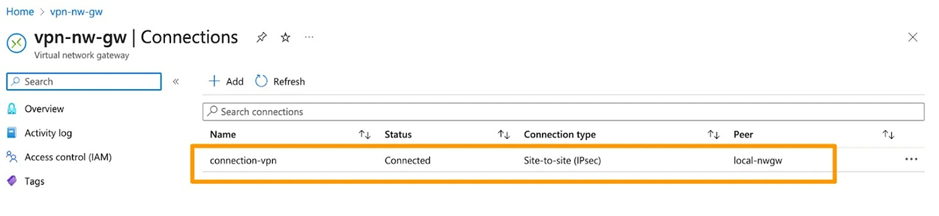
11. Now, check if the status is shown as connected on Azure and up on AWS.
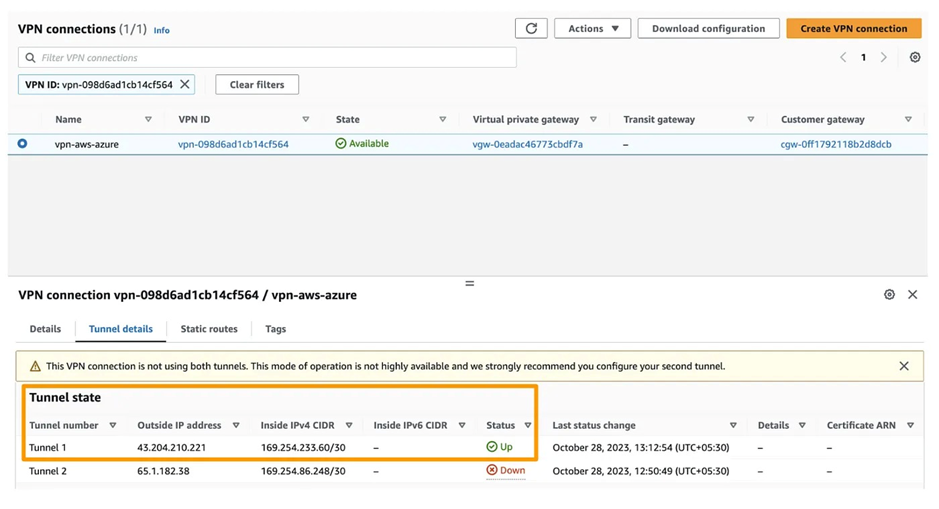
12. Do the same for tunnel 2 and navigate to step 9.
13. Edit the AWS VPC Route table. Include the Azure VNET’s Subnet CIDR range (subnet-01) established in Step 02 as the Target for the Virtual Private Gateway.
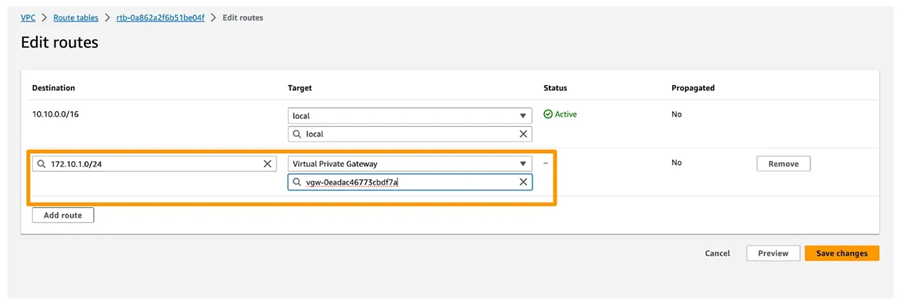
14. Your Site-to-Site VPN is all set.
15. Create Azure and AWS resources under created RG and VPC to test it.
Which IP Range To Use For VPN:
Azure Vnet-1 CIDR = 10.0.0.0/16, Subnet-1 = 10.0.0.0/24
Azure Vnet-2 CIDR = 10.1.0.0/16, Subnet-1 = 10.1.0.0/24
Azure VGW Subnet Range = 10.0.1.0/24 (It should be under CIDR, but should not match or overlap other subnets in Vnet) same for Vnet-2
Azure Local Network Gateway (LGW) uses AWS VPC CIDR ranges to Address Space
=====================================================================
AWS VPC CIDR = 10.10.0.0/16, Subnet = 10.10.0.0/24
Or use this Ranges CIDR = 172.10.0.0/16, Subnet = 172.10.0.0/24
AWS CW uses the IP address of Azure VGW
AWS VPN Connection uses Azure Subnet-1 range in Static IP prefixes
For more information, connect with itechops.
References:
Site-to-Site VPN: Connecting AWS to Azure | by The MLOps Guy | Medium
0 Comments