Microservices Security: Protecting Your Data In A Decentralized System
If you are aware of the digital world and consistently stay updated about the recent nuances, then you must have heard about microservices security. What does it mean, and how does it protect your data in a decentralized system? The adoption of microservices security has become quite widespread. This is mainly due to its scalability, flexibility, and even rapid approach.
Usually, in a decentralized system, data is distributed across different services, which can easily tamper with security. Microservices security helps prevent this security breach effectively.
Analyzing The Meaning Of Microservices Architecture
Before we talk about the methods and the benefits that microservices security brings with it, let us first understand the architecture. In this system of software development, a complex application is usually decomposed into smaller and independent services. You can develop, deploy, and even scale each of these independently.
Each service will be responsible for a unique business function. Communication is via services like APIs. Microservices architecture follows the same pattern as that of a construction worker.
Just like a construction worker needs to layer concrete to provide a strong base, the same principle can be applied to microservices architecture.
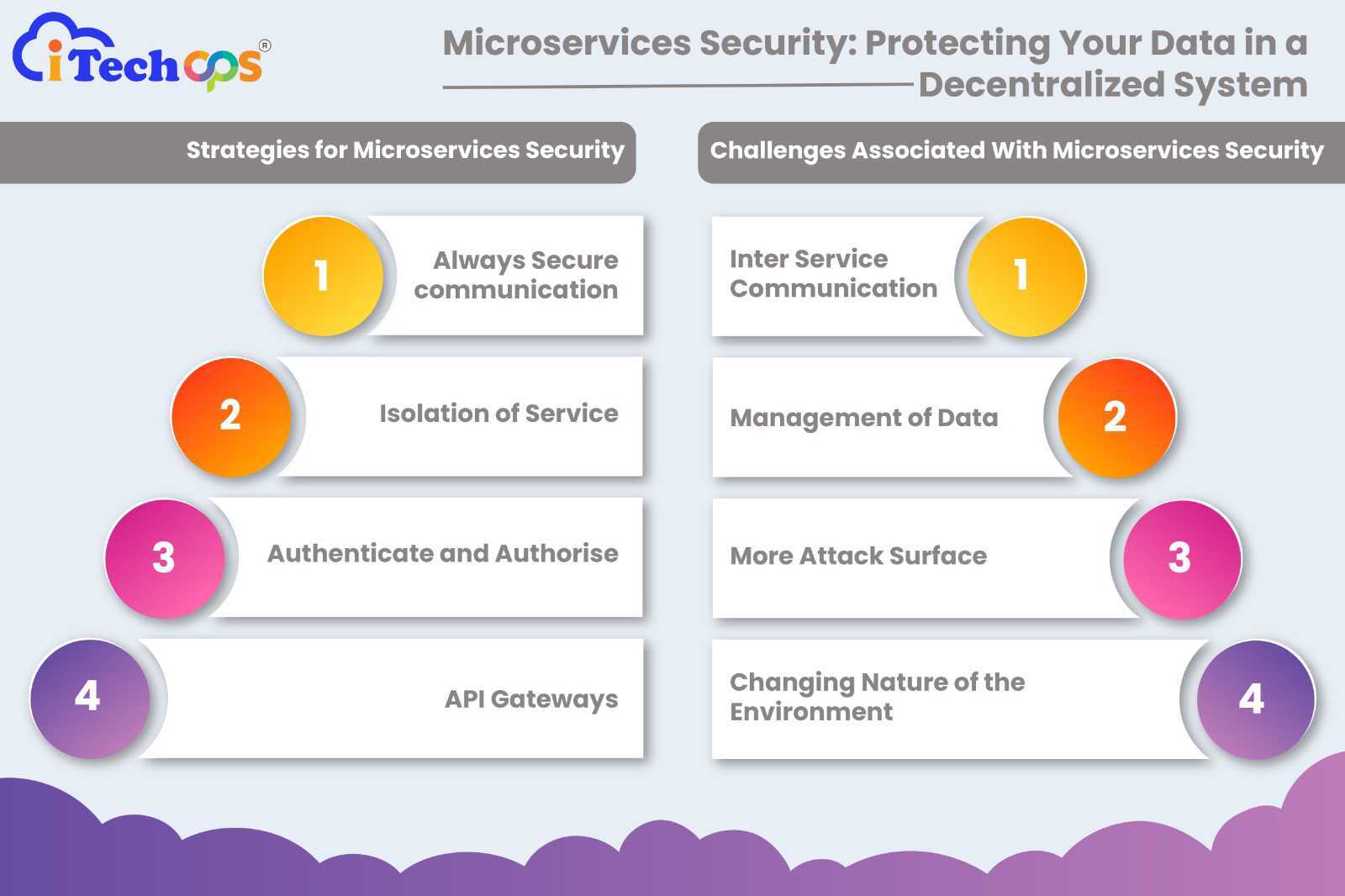
Strategies For Microservices Security
How can you implement the best microservices security to protect your data in a decentralized system? Some of the best strategies that you can keep in mind are:
Always Secure Communication
To ensure that you can maximize data confidentiality, one of the most important factors to keep in mind is securing the communication between services. How can you do that? Try to implement transport layer security, popularly known as TLS. You can choose to implement a mutual TLS for service-to-service communication.
This will certainly help you authenticate the client and the server. You can also choose to curb any man-in-the-middle attacks that are extremely common in a decentralized system.
Isolation Of Service
Isolation of service is imperative, and this usually encompasses three major types of isolation – physical isolation, logical isolation, and even network segmentation.
● Physical Isolation—Always try to deploy services on distinct servers and even containers. This will reduce the chances of a breach and keep the extent of damage under control.
● Logical Isolation—It is always suggested that both API gateways and even service meshes be employed. They tend to act as mediators and can control the flow of requests between services. They can also control and govern the fact that only authenticated requests reach out to servers.
● Network Segmentation –Isolation of service is also possible with the help of network segmentation. You can use virtual networks, firewalls, and sometimes even VPNs to act as a wall of security. It can secure the channel and also mitigate the possibility of any risky attacks.
Authenticate And Authorise
One of the most important strategies for microservices security is authentication and authorization. Always remember to implement a very strong authentication mechanism to verify your users. Try to use mediums like OAuth or JWT, as these are quite reliable. These are the best options for the token-based authentication system. On the other hand, fine-grained authorization is also equally necessary.
For the same, you can use Role-Based Access Control, popularly known as RBAC, or Attribute-Based Access Control, or ABAC. Such a system ensures that users or services access only those that are instrumental for their functioning.
You can also use a centralized identity management system, which helps you easily manage users’ identities and credentials. It is the best system for maintaining consistency in authentication.
API Gateways
One of the most important roles in microservices security is incorporating a secured API. A secure API can guarantee the confidentiality of information and make it visible to only those users, apps, or even networks that have the authorization.
The API gateway acts as a single entry point for clients. It can help you enforce the right security policies and reduce complexity by easily managing security across various services. For ultimate efficiency, always ensure that your API has the following characteristics: integrity, availability, confidentiality, and reliability.
Benefits Of Microservices Security In A Decentralized System
Navratri has a good idea about microservices security and the best strategies to adopt; it is important to analyze the benefits you can expect. Some of these are:
● Microservice security can help you to increase productivity and speed. This is because multiple teams can start work simultaneously on the various elements of a distributed system.
● Always let the developer teams select specific components of the architecture. This will help you to ensure smooth functioning and avoid any extravagant disruptions.
● Each microservice can be deployed and scaled independently. This can allow you to utilize resources more effectively and handle the different loads of work.
● Microservices enable decentralized decision-making. This helps teams to take ownership of specific services and design choices better.
Challenges Associated With Microservices Security
Microsoft Security is beneficial as it can improve agility and scalability. However, some of the security challenges that this type of security might pose are :
1. Inter-Service Communication
You have to ensure that communication between various services is secure. Microservices security opens up many channels, which can compromise communication security and lead to data breaches. It can also contribute to unauthorized access, which can compromise security factors.
2. Management Of Data
One characteristic feature of multiservice security is that data is distributed across multiple services. This might make it difficult to ensure consistency, disrupt security controls, and maintain complete data integrity.
3. More Attack Surface
In the context of microservice security, you will notice that multiple services communicate with each other. Hence, with such communication, the surface area of the attack may widen as well. This opens new opportunities for attackers to carry out malicious activities and cause security data breaches.
4. Changing Nature Of The Environment
The environment for microservices is dynamic. This means that it is constantly changing with the addition, update, and removal of services. This makes it slightly more difficult to maintain security and consistency simultaneously.
Conclusion
When you are dealing with a decentralized system, protecting your data is extremely important as it can lead to long-term implications. It will not only help you to safeguard against cyber threats but also ensure regulatory compliance. With the help of simple strategies like authentication and authorization, isolation of services, and even API gateways, you will be able to gain maximum efficiency. When it comes to microservices security, it is important to understand that it is an ongoing process. Continuous assessment, as well as adaptation of new methods, is important to disseminate the possibility of any attacks. Itechops can help you better with clarification of your doubts.

0 Comments